With the trend of applying information systems to all production activities of enterprises, deploying a network system when establishing a business has become essential.
So, what is an enterprise network?
An enterprise network is considered the backbone for communication between computer connections and related network devices (even smartphones) across departments within an organization. An enterprise network can help reduce complexity by simplifying various communication protocols.
Enterprise Network Architecture Model
As networks become more sophisticated, a modular approach is used to design the access layer, distribution layer, and the core of both WAN and LAN networks.
The modular design method is seen as a complement to the Hierarchical design method. In large-scale network systems, there are generally multiple network zones serving different activities and functions. Designing by modules for a large network infrastructure—by separating network areas with distinct functions—is also a widely used method in designing enterprise network infrastructures for businesses, companies, and large organizations (referred to collectively as Enterprise).
The Modular design method can be divided into three main areas, each created from smaller network modules:
– Enterprise Campus: Includes the modules required to build a high-availability, flexible, and scalable campus network.
– Enterprise Edge: Aggregates connections from various components at the edge of the Enterprise network. This functional area filters traffic from the modules in the Enterprise edge and sends it into the Enterprise campus. It includes all the components necessary to ensure effective and secure communication between the Enterprise campus and external systems, partners, mobile users, and the Internet.
– Service Provider Edge: The modules in this area are deployed by service providers, not part of the Enterprise. These modules enable communication with other networks using various WAN technologies and ISPs.
Network Components and Functions in Cisco’s Specialized Architecture
- Enterprise campus area
- Enterprise data center module
- Enterprise branch module
- Enterprise teleworker module
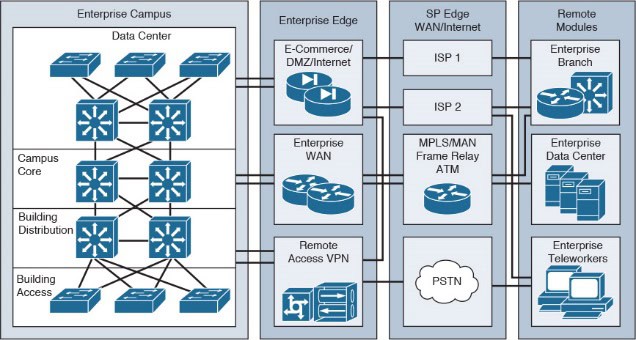
Cisco Enterprise Network Architecture Model
Cisco’s typical enterprise network architecture model retains the concepts of distribution, access, user connection components, WAN services, and server stations via a high-speed backbone network. In smaller networks, the layers may be combined into a single layer or even a single device, but the functions remain unchanged.
Within the enterprise infrastructure, it includes the core field, builds the distribution and access layers, with a data center module. The edge area connecting to service providers includes Internet access, e-commerce, VPN, and WAN modules. The service provider edge offers Internet routing services, public switched telephone network (PSTN), and WAN services for the enterprise.
1. Enterprise Campus Module
Includes the following sub-modules:
- Campus core
- Building Ditribution
- Building Access
- Server farm/data center
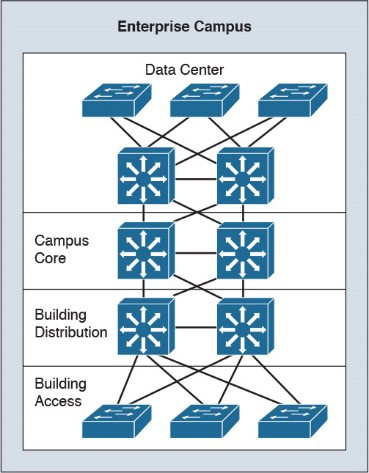
Enterprise Campus Model
The Core layer provides a high-speed switching backbone between buildings, server systems, and inter-enterprise connections. This segment includes redundancy connections and fast convergence. The Distribution layer is responsible for access switching and control, QoS, redundancy routing, and load balancing. Building access switches allow VLAN access, PoE for IP phones and wireless access points, and prevent Broadcast and Spanning Tree issues.
The Server farm/data center enables high-speed and high-availability access (redundancy) to servers. Enterprise servers such as file and print servers, application servers, email servers, Dynamic Host Configuration Protocol (DHCP) servers, and Domain Name System (DNS) servers are located in the server farm. Cisco Unified Call Manager servers are located in the server farm for IP phone networks. Network management servers are also placed here but must be connected to each module within the enterprise to provide network monitoring, logging, and configuration management.
Enterprise infrastructure can be applied to small, medium, and large sites. In most cases, large-scale networks use a three-layer design with access layer, distribution layer, and core layer. Smaller sites may use a two-tier design with access and integrated core-distribution layers. It also allows configuring distribution functions in a multi-access device to maintain fast communication on the backbone. Medium-sized networks may use either a two- or three-tier design depending on port count, service demands, performance, and adaptability requirements.
2. Enterprise Edge Area
Includes the following sub-modules:
- E-commerce networks and servers
- Internet connectivity and demilitarized zone (DMZ)
- VPN and remote access
- Enterprise WAN
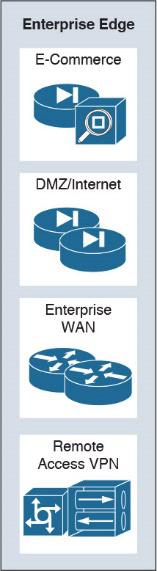
Enterprise Edge Area
2.1. E-Commerce Module
The e-commerce submodule at the enterprise edge provides a highly available network for business services. It uses a highly adaptable design of the Server farm module combined with the Internet module’s connectivity. Devices in this submodule include:
- Web and application servers
- Database servers: Store application data and transaction information
- Firewalls and firewall routers: Manage communication between users in the system
- Intrusion Prevention Systems (IPS): Monitor critical network segments to detect and respond to cyber attacks
- Multilayer switches with IPS modules: Provide traffic handling and integrate security monitoring
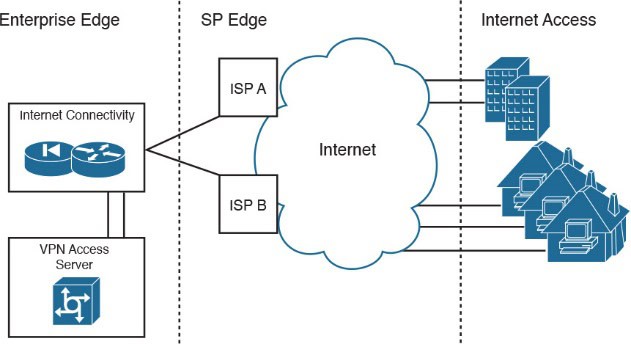
2.2. Internet Connectivity Module
The Internet submodule in the enterprise edge provides services like public servers, email, and DNS. It connects to one or more Internet service providers (ISPs). Components include:
- Firewalls and firewall routers: Protect network resources, filter traffic, and offer end-point VPN services
- Internet edge routers: Provide basic filtering and multi-layer connections
- FTP and HTTP servers: Support web applications allowing the enterprise to communicate with the outside world via the public Internet
- SMTP relay servers: Act as intermediaries between the Internet and internal mail servers
- DNS servers: Resolve domain names and forward requests to the Internet
The simplest connection form is a single direct link between the enterprise and a service provider. The downside is no redundancy in case of network failure.
Direct Enterprise to Service Provider Connection
Multihoming solutions can be used for redundancy or failover internet services.
Internet Multihoming Options:
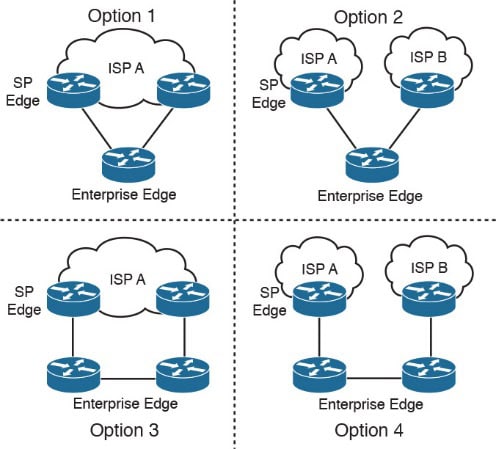
multihoming Internet options
Các tùy chọn multihoming Internet:
- Redundant connection paths but no ISP or internal router redundancy
- Redundant paths and ISPs but no internal router redundancy
- Redundant paths and internal routers but no ISP redundancy
- Full redundancy of internal routers, link paths, and ISPs
2.3. VPN/Remote Access
The remote access or VPN module of the enterprise edge provides anti-intrusion remote access services, including remote user authentication. Submodule components include:
- Firewalls: Filter traffic, authenticate remote endpoints, and provide connections via IPsec tunnels
- Cisco Adaptive Security Appliances (ASA): Authenticate remote users, provide firewall and intrusion prevention services
- Intrusion Prevention Systems (IPS): If remote users access via PSTN, VPN is implemented at access endpoints. Current networks often deploy VPN on access-endpoint servers dedicated to WAN links. VPN reduces communication costs by leveraging SP infrastructure. Remote offices, mobile users, and home offices access the Internet using local ISPs with IPsec tunnels to the VPN/remote access submodule via the Internet submodule.
VPN Design
2.4. Enterprise WAN
WAN technologies include:
- Multiprotocol Label Switching (MPLS)
- Metro Ethernet
- Leased lines
- Synchronous Optical Network (SONET) and Synchronous Digital
- Hierarchy (SDH)
- PPP
- Frame Relay
- ATM
- Cable
- Digital subscriber line (DSL)
- Wireless
When designing the enterprise edge, consider:
- Identify necessary connections for Internet access – the Internet connectivity module handles this task
- Create e-commerce modules to allow customers and partners to access business services and database applications over the Internet
- Design remote access or VPN modules for internal network access via VPN from the Internet. Implement security policies and authentication configurations
Meeting the Challenges of a Future-Oriented Network
To build a future-oriented enterprise network, companies must address several key challenges. They need to integrate and manage diverse technologies and resources into a unified, efficient network that meets users’ growing data needs. In addition to delivering high performance and reducing costs, next-generation enterprise networks must be flexible, highly scalable, easy to manage, and secure to meet future demands.
1. Flexibility is the Key to Next-Generation Networks
Traditional networks were designed for speed rather than flexibility, but that approach is no longer suitable as cloud-based services are becoming the standard. To achieve greater agility and adaptability, companies need to shift from traditional, static, device-centered network planning, deployment, and management to a dynamic, on-demand model that enables them to rapidly scale or adjust services to meet business demands.
2. Scalability to Meet New Business Demands
A future-ready network must place the user experience at the core by developing and implementing user and application-centric network management policies to address issues such as congestion and performance.
An enterprise network ready for the future must be scalable enough to quickly deploy IT services and applications that support business needs. At the same time, users expect to connect to network resources from both wired and wireless devices.
To meet these demands, enterprise networks must be scalable to handle capacity requirements across data centers, wide area networks, campus networks, mobile Internet, IoT, and other network infrastructures.
3. Simplifying Network Management
With increasing convergence among enterprise networks, mobile Internet networks, and IoT networks, companies need to enhance intelligence at the network edge to optimize data traffic and enforce policies without compromising security or service quality.
4. Strengthening Cybersecurity
With the rapid evolution of advanced persistent threats (APTs) and changes in cybersecurity architectures, managing network security has become increasingly complex and critical—leaving no room for compromise.
Today’s businesses must establish systems capable of monitoring and responding to cybersecurity threats in real time to protect their networks against increasingly sophisticated intrusion attempts.
To address the evolving threat landscape, advanced and comprehensive network security technologies and approaches must be adopted, such as sandbox-based APT detection, unknown threat analytics, and mitigation of DDoS attack modes.